HOME | ABOUT US | MEDIA KIT | CONTACT US | INQUIRE
HOME | ABOUT US | MEDIA KIT | CONTACT US | INQUIRE
If you’re a business owner or executive who’s sleeping like a baby at night, Rob Arnold offers this elbow to the ribs that might keep you up for a spell:
“What we’re seeing is a dramatic shift in attack patterns to target small-and medium-size companies.” — Bill Swearingen, Co-Founder, SecKC
“The interconnectedness of all business activities today, coupled with the increasing reliance on technology to delivery even ordinary services, makes everybody vulnerable” to on-line attacks, says Arnold, an information security officer at the University of Kansas. And here’s why: “Even if you don’t think you’re sitting on a mountain of data,” Arnold cautions, “your credit-card processor is. Your utilities are. All the big service providers are in the process of shoring up defenses, even as business owners who consume services are attempting to shore up theirs.”
Because in the parlance of IT security these days, Arnold says, business is in an arms race with the bad guys. And the bad guys aren’t taking prisoners.
Instead, they’re driving the pain farther down the business scale, avoiding the big IT security budgets of large organizations and lasering in on smaller businesses that lack both the resources to assure peak vigilance—and in too many cases, the sophistication to appreciate the gravity of the threat.
“A lot of organization might think that because small, they aren’t a target, but everything from work stations to servers to POS machines is,” said Mike Hogan, a cyber-security specialist for Honeywell. “Just because they’re small doesn’t mean they’re not going to be affected by these kinds of attacks. If you’re vulnerable, you’re going to be exploited at some point, and data that is compromised can be more damaging to a small business.”
One might not consider the White House in Washington to fall within the category of those lacking resources, but an egregious lack of sophistication was on display in October when officials learned that the non-classified computer systems at 1600 Pennsylvania Avenue. Worse, they couldn’t tell who was behind the attack, or how long it had been going on. And worse yet, they didn’t even know they’d been infiltrated until they were tipped off by an ally who spotted evidence of the intrusion during its own security operations.
That’s a damning indictment of how lax the nation has been with regard to a continuing threat, in a country full of business executives who believe the headline-making security breaches at Target or Home Depot mean his smaller company isn’t on anyone’s hit list.
“What we’re seeing is a dramatic shift in attack patterns to target small-and medium-size companies exactly because they don’t have the large IT shops, the high-end protection equipment, the intrusion protection or next-generation firewalls,” says Bill Swearingen, an IT security professional from Olathe who co-founded a network of like-minded interests calling themselves SecKC. “Honestly, a lot of times, there’s no IT department, no outsourcing and no security built into the process at a lot of small companies,” he said.
The last five years, Swearingen said, have marked a dramatic shift in the attack profiles, moving away from the image of a guy in Eastern Europe hacking away at big security systems from the safety of an overseas basement.
Now, they are not probing systems, they’re probing people.
“Those attacks on a Web page or server or network, trying to break in through a firewall, that kind still exists, but that’s not really the trend these days,” he said. The goal of the crooks is to get data—credit-card data, corporate secrets, health records or company financials—and as a thriving IT security sector has devised new and better defenses, the attacks have morphed to follow the next logical weakness. “The trend is to attack people—employees, like me, you and everyone else, mainly because people have access to data,” Swearingen said. “The easiest way now is to attack people who have access: Phishing, sending e-mail asking for a username/password, or asking you to install software. The end goal is the same: to compromise your machine and to use your access to get further into the company’s data.”
And they can be quite creative in the process. Bankers, for example, have set up elaborate security systems, only to test the creative powers of their foes. Something as simple as a CD that appears to have been accidentally dropped on the floor—with a label reading “Monthly payroll figures”—is a mighty tempting target for inquisitive employees, who might not give a second though to popping it into a computer drive. Boom: Automatic download, instant access.
All of this is scary enough with where interconnectivity is these days. But at the dawn of the Internet of Things, where your home security system—even the stove in your kitchen—might have an IP address, the world of technology is creating doors for access that haven’t yet been judged secure.
Take building-automation systems. Marc Petok, of Lee’s Summit-based Lynxspring, has written extensively in security journals about new and emerging threats. Those systems these days control HVAC systems, door locks, manufacturing machinery, pipeline systems carrying all manner of volatile materials or gasses—
you name it.
His touchstone reference is from the James Bond movie Skyfall, there the bad guy hacks the building systems at Bond’s workplace, turns on the gas and supplies a spark, with devastating and deadly consequences. It’s Hollywood to us, but it’s something far more realistic to the Marc Petoks of the world.
“Can people get into these systems to do things? Yes, absolutely,” Petok warns. “It can be deadly things like that, or as people get into those systems and sit there, they can eventually steal data, information, whatever it is.”
So how much of that is going on? No one really knows, he says. After all, if you were a company executive who’d been thusly compromised, would you want to admit it publicly? “It’s what you don’t know, that’s dangerous, where somebody is in my network,” Peteok says.
“That’s the whole thing with cyber-security,” he says. “As it starts to evolve, what I’m seeing is that there will be certain industries where it will be mandatory for you to say if there were any cyber-security issues, especially financial and health care. Those rules will follow. We don’t know what we don’t know at this point, but I see it going on over and over and over again.”
For those who think they’re too small or inconsequential to be targets of a foreign attack, Petok suggests you think about ice cream. “If they are on the network, they are exposed, yes,” he says, citing the October news that computers at Dairy Queen had been compromised. What do they have of value? “You have to look at every entry point. Let’s say a pizza place is hooked up to a provider of their flour or tomato sauce—that is a pivot point to get into a supplier’s network. It’s almost like a daisy chain.”
And if you think it far-fetched that someone’s thermostat could be a portal into records from the utility company, or the bank that processed last month’s energy payment, these IT pros offer some sobering guidance:
“They’re coming out so fast with new technologies and systems that researchers don’t have time to analyze them or give them enough of a review,” Swearingen said. “We’re kind of catching up with those devices, and we’re finding out what you’d expect: They’re made as low-cost as possible, generally with very little security consideration taken, they’re very easy to compromise or very vulnerable to attack. Yes, it is a big threat.”
Fortunately, all involved say, there are steps that smaller businesses can take to address the threat, and many of those are affordable, even free. Those steps tend to be grounded in an operational imperative everyone should embrace today: Awareness.
“As the whole idea of cyber-security is being exposed—when you read about Target, Dairy Queen or the nude pictures of stars where somebody hacked a phone account—as more of that connects and resonates with people, the industry as a whole is addressing the issue with new technologies, new cyber protections,” Petok said. “Ultimately is anything completely bulletproof? No, but I want to make it hard as hell for somebody to hack into what I have.”
In the end, said Honeywell’s Hogan, vigilance is the key.
“The risk level extremely high. If you have a presence, you’re a target, from state-sponsored actors to organized multinational hackers to the guy down the street looking for kicks,” Hogan said. “There are hundreds of thousands out there with malicious intent—they’re after your money, your information, your resources, and they are creative. They’re constantly lurking. So it’s up to all security professionals to stay abreast of what the new methods of attack are.”
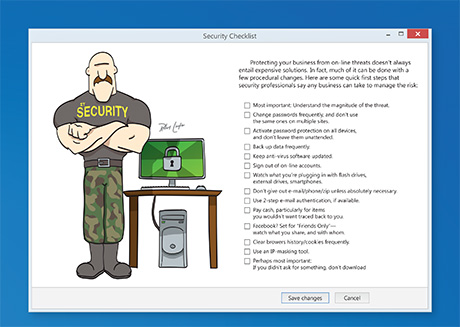
Protecting your business from on-line threats doesn’t always
entail expensive solutions. In fact, much of it can be done with a few procedural changes. Here are some quick first steps that
security professionals say any business can take to manage the risk:
Protecting your business from on-line threats doesn’t always entail expensive solutions. In fact, much of it can be done with a few procedural changes. Here are some quick first steps that security professionals say any business can take to manage the risk
• Most important: Understand the magnitude of the threat.
• Change passwords frequently, and don’t use the same ones on multiple sites.
• Activate password protection on all devices, and don’t leave them unattended.
• Back up data frequently.
• Keep anti-virus software updated.
• Sign out of on-line accounts.
• Watch what you’re plugging in with flash drives, external drives, smartphones.
• Don’t give out e-mail/phone/zip unless absolutely necessary.
• Use 2-step e-mail authentication, if available.
• Pay cash, particularly for items you wouldn’t want traced back to you.
• Facebook? Set for “Friends Only”—watch what you share, and with whom.
• Clear browers history/cookies frequently.
• Use an IP-masking tool.
• Perhaps most important: If you didn’t ask for something, don’t download